Biometrics in Digital Identity – A Primer, Part 1/2
Driven by advances in biometric technology, biometric identification is now ubiquitous. From employee ID to National ID, and access control at housing societies to airport security, the use of biometric identification and authentication is growing rapidly. Even in personal spaces such as smartphones, biometrics-based log in solutions have grown, with 77% of smartphone devices now using fingerprint or face biometrics to enable access. Encryption keys, passwords and passcodes are being replaced with biometrics faster than ever. Computer Science experts predict that the range of options currently available to the consumer in terms of biometric modalities used and the way we use them will only expand.
In the first of the blog series on biometrics, we present a primer on the basic concepts and terminologies that we will keep returning to. We believe that this is necessary to fully understand the debate on the role of biometrics in digital identity. Through the blog series, we hope to unpack various dimensions of the debate, identify unanswered questions, ideate on current solutions, and explore how such technologies can be safely leveraged to meet the objectives of UNDP’s Sustainable Development Goals (SDGs).
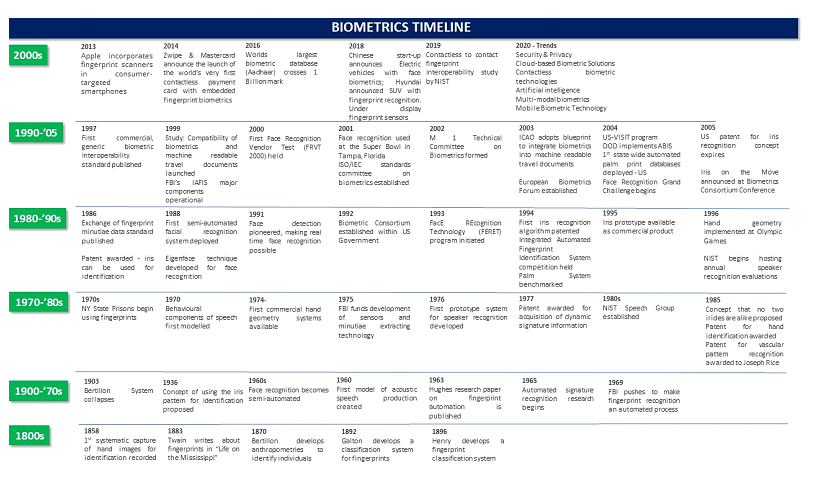
Derived from the Greek words ‘bio’ (life) and ‘metrics’ (to measure”, biometrics (\ ˌbī-ō-ˈme-triks \) is defined as the measurement and analysis of unique physical or behavioural characteristics to verify personal identity. The physical characteristics pertain to the individual and include fingerprints, facial features, iris patterns, and even DNA.
Behavioural characteristics are related to the way a person behaves. The manner in which one speaks, writes or walks (gait) which differentiates him/her from others is associated with the person’s behaviour. Some of the characteristics are a blend of physical and behavioural aspects. For instance, the voice of a person is mostly behavioural. However, it depends upon physical aspects such as age, health, and size of oral cavity among others. These unique physical or behavioural characteristics can help identify a person or verify personal identity. Globally, dedicated scientific streams are working on each of these characteristics, but their effectiveness and usability vary significantly. Before we discuss a few of the characteristics and what makes them unique, let’s try to understand some of the terminologies.
Identification, Authentication, and Authorisation
Identification, Authentication and Authorisation are terminologies that are often used interchangeably. However, they are different.
Logging in to an email account requires three logically sequential steps:
1. Identification: The login page asks ‘who you are’, and you respond with your email ID which could be your name or a random ID that you had selected while setting up the account. For the email platform, you are identified as the User ID. However, you will still need to authenticate yourself to access your emails.
2. Authentication (Verification): After providing your email ID, you are required to key in your password and further ‘authenticate’ yourself. In general, the system challenges you to ‘prove who you are’ by producing something unique that you possess which the system can verify or through a shared secret that you have such as a password.
3. Authorisation: Once you are through with the authentication, you are ‘Authorised’ to access your emails.
<Image Suggestion>: Someone entering a user id and password on the screen.
Governance in large organisations with more people than can be recognized through facial memory recall requires some form of unique identification and identity verification process during transactions.
Typically, in developed countries, modern primary health centres are well distributed. Almost all newborns are born in such health care facilities and issued birth certificates. The time and place of birth (location) recorded on a birth certificate makes the person unique in the country’s civil registry system. The ID systems in such countries (with ~100% coverage of civil registry systems) leverage the birth registry system for uniqueness and build their ID system thereon.
In developing countries, the reality is a bit different. The penetration of primary health centres is nowhere close to 100%, and the vast majority of newborns are born at home. The issuance of birth certificates and coverage of the civil registry system is also short of 100% coverage. The advancement of biometric technology over the last decade has enabled such countries with populations as large 1B+ to uniquely leverage the technology to uniquely identify people based on their biometrics and further good governance with foundational identity systems.
Foundational identity systems use identification mechanisms to ensure the uniqueness of identities in a system. They compare a combination of biometric and demographic information of a candidate against what exists in the system. If a match is found, the candidate is considered as a potential duplicate and rejected after due deliberation.
Countries that collect biometrics as a requirement to establish uniqueness in their foundational ID system can further leverage the biometrics for authentication.
Biometric authentication is generally a 1:1 approach. Foundational identity systems register a resident by storing and recording his/her unique biometric and demographic information in the system, and by issuing an ID (national ID number) against it. When the resident needs to prove his/her identity at a later stage in a different context or circumstance, the ID and a combination of demographic and/or biometric information are passed through the system. The incoming information is matched with pre-existing records for the same ID. A successful match (authentication) grants the resident access (authorization) to the service that the s/he initially wanted to avail of.
<Image Suggestion>: Fingerprint with a tick mark or some access being granted
Both offline and online authentication mechanisms are possible. During online authentication, the match happens in a central location where the identities or biometrics are stored as part of the registration process. There are decentralised authentication models, where the information pertaining to a subset of the population is made available for the match. Offline authentication uses alternate arrangements for a local match such as biometric smart cards and QR codes, where matching happens locally.
Biometric Modalities
Artists usually leave behind some kind of secret signature on the art they produce. Cavemen used ‘fingerprints’ to ‘sign’ their cave paintings. Indeed, biometrics date back beyond the prehistoric era to the age of the Neanderthals, evidence of which is found in the Panel de las Manos at El Castillo, the earliest known cave art. A handprint in these cave frescoes resulting from a prehistoric artist blowing pigment against his/her hand created the first indelible signature of the artist and is estimated to be at least 37,300 years old. It is interesting to note that Neanderthals and later, the prehistoric cavemen were already aware of the uniqueness associated with fingerprints and wanted to leave a personal and distinct mark on their paintings which they believed could not be imitated or duplicated easily.
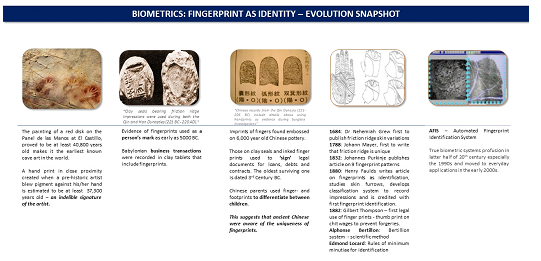
Fingerprints were used in Babylonia (~1500BC) to execute contracts written on clay tablets which were signed by both parties. One could consider this as the first form of ensuring non-repudiation using biometrics against handwritten signatures. Studies on biometrics started early on in the written history of humanity. The stream has evolved, transforming itself into a robust and reliable scientific platform for various identification or authentication requirements.
While there is a plethora of biometric modalities available, only a few have proved to be useful in identifying and authentication use cases. Let us explore some of them and see what makes them unique without comparing their effectiveness, usability, risks, or reliability.
Fingerprint Recognition
Fingerprints are nearly always unique, difficult to change, and less vulnerable to aging unlike a person’s face. They, thereby, inspire confidence as a reliable biometric. The most popular of all biometrics for a long while, fingerprint recognition is truly standalone due to the ease of use, reliability, and advanced technology stage at which it operates.
Let’s see what makes a fingerprint unique. The human skin is made up of three layers. The raised portions of the skin’s outer layer on human fingers and toes are called friction ridges while the low lines between them are called valleys. When friction ridges leave their impression on a surface, fingerprints result. Fingerprint technologies focus on capturing this unique pattern, leveraging it for identification or verification purposes.

Iris and Retina Recognition
Iris and retina recognition are generally categorized as ‘ocular-based’ technologies which are less vulnerable to aging or alteration. The retina contains light-sensitive cells and nerves to collect visual information. The patterns of the retina’s blood vessels are unique which retinal scans take advantage of.
The iris is the colored ring-shaped region in the eye whose patterns are unique and different. Today, iris recognition is considered to be one of the most reliable and accurate biometric modalities available. <Image Suggestion>: Iris Image
Facial Recognition
Many unique features are associated with the face. Traditional facial recognition algorithms focus on the relative size, shape or position of the eyes, cheekbones (which give a structure to one’s face), nose, and jaw. There are three-dimensional face recognition sensors that can assess the face’s third dimension (depth) features such as the eye sockets and size of the nose. Skin texture analysis is another approach where the unique lines, patterns, or spots on someone’s face are converted to digitally verifiable representations.
<Image Suggestion> : Face Image
Voice Recognition
Multiple parts of the human body are involved in producing voice including the vocal cords, throat, nose, mouth, and larynx structure. Since these are physical and unique aspects of the human body, the sounds produced by their orchestration is also unique. When sounds are clubbed with a person’s behavior, be it speech delivery or the volume of the voice, the resultant combination is particular to that individual. Voice biometrics capture multiple attributes of the voice to arrive at the voiceprint of a person. Acquisitions are done by asking the person to read out a fixed text or a set of numbers or to speak something completely random based on the algorithms used. This voiceprint is then used for identification or authentication requirements. Unlike the iris or fingerprints, a person’s voice is expected to change over time. <Image Suggestion>: Voice biometric
DNA Recognition
Deoxyribonucleic acid contains a unique genetic code or a blueprint of a human body. DNA is composed of a series of smaller molecules within. The order in which the smaller molecules are arranged makes for the uniqueness of each individual. The extraction of DNA characteristics or DNA analysis is a highly time-consuming and expensive activity. In addition, DNA may not be an effective modality in distinguishing monozygotic (identical) twins. However, it provides the most reliable identification and is therefore used in forensics. <Image Suggestion>: DNA Image
Other biometric modalities include:
● Hand/Finger Geometry – geometric features such as finger length or hand width
● Signature Recognition which could be static (visual comparison of signatures) or dynamic (how the signature is made on a specific signing device)
● Gait Recognition – an individual’s walking style
● Typing Recognition – rhythm/pattern of typing
● Electrocardiogram – measurement of heartbeat pattern
● Palm Prints Recognition – combination of fingerprints and hand geometry
● Finger Vein Recognition – vein patterns beneath the skin’s surface
● Ear Recognition – shape of the outer ear
We will continue the conversation in Part 2 of this series ‘Choosing a biometric modality for digital ID systems’.
Do stay tuned!

